Greetings
Reader, Here I come up with another interesting article / blog post
about the vulnerability that I found on ESEA (https://play.esea.net)
almost a month before. Where a web app functionality causing two
critical vulnerabilities SSRF (Server Site Request Forgery) and other
one that can allow attacker to grab IP address of any user. However both
the issues are different and reported different but causing by same
functionality. This one is interested finding so I made up my mind to
write up about this issue. So lets begin-
Vulnerable Domain - https://play.esea.net
Vulnerability Name - SSRF and Grabbing users IP address
About Target Domain - E-Sports Entertainment Association League (ESEA)
is an esports competitive video gaming community founded by E-Sports
Entertainment Association (ESEA). It is widely known for their
anti-cheat software. ESEA features a system that allows players of all
levels to play matches with others.
ESEA
provide guestbook to every user where other users can post (comment)
anything only if it is unlocked and same commenting functionality
provided on forum posts, news posts and user's account (guestbook). This
is where the issue occurs. If user posted any link/URL that contains an
image such as http://example.com/image.jpg then moving mouse on that
link shows the thumbnail of that image. For example user posted a link
in comment such as http://site.com/rat.jpg then move your mouse on the
link that you posted, will shows a small thumbnail on ESEA website. This
is happening because the link automatically executing in case of
creating a thumbnail of image.
So
another question may arise, why they required such functionality?
Initially ESEA allows to post video (gameplay) from YouTube for some
contests. So this functionality shows the thumbnail from YouTube video
and later I noticed, it is working on image URL as well.
As
I confirmed the image URL executing automatically so this is the
perfect place to test SSRF. That mean If
http://sitename.com:80/image.jpg shows the thumbnail in the guestbook by
moving mouse on it then site as http/80 port is open. But if we found
it closed ports like http://sitename.com:32564/image.jpg, as port is
closed the output will not be displayed.
http://sitename.com:80/image.jpg=> It gives an output (Port 80 is open)
http://sitename.com:32564/image.jpg => No output (Port 32564 is closed)
http://sitename.com:80/image.jpg=> It gives an output (Port 80 is open)
http://sitename.com:32564/image.jpg => No output (Port 32564 is closed)
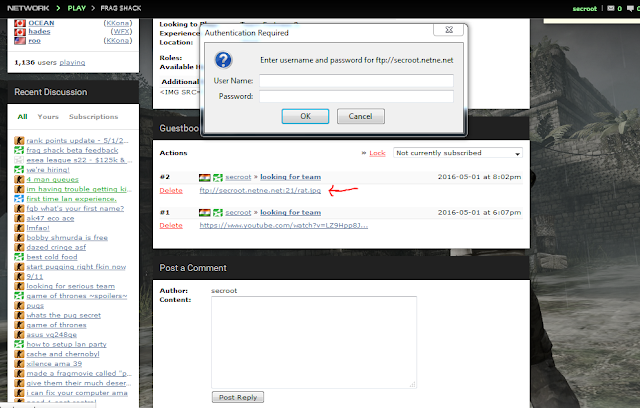
As you can check in below image, FTP port 21 automatically executing. It doesn't sanitizing the input.
So
after formalities and procedure they verified and resolved this
vulnerability and later stage port number filtered and doesn't executing
anymore. And I got reward $500 for this bug + 500 ESEA points + Profile
badge.
But but... One thing left
But but... One thing left
After
fixing SSRF, I noticed that the URL still executing only with HTTP and
HTTPS and the thumbnail still appears so I thought to use GIF image to
grab user's information. So I crafted a GIF to grab user's information
such as IP address, user agent then pasted the link on guestbook. Next
time when I refreshed the page, I found the GIF image URL successfully
executed that mean it created a log into log file. Later I tried to use
http://iplogger.org/ to easy my task and it perfectly worked.
This vulnerability is pretty simple with critical severity and allowed me to grab information of user from guestbook, forums and news. Suppose in case of grabbing users information you just need to paste it where the most of users visit frequently such as latest news section, latest forum posts or if you want to target any particular user then all you have to do is to paste the link in victims guestbook so whenever the user visit his/her guestbook will be a victim.
First they rewarded me $500 for this bug + 500 ESEA points + Profile badge.
but later they increased the payout to $750 -
After submitting this issue they fixed as soon as possible. And I'm glad to work with them. They are really dedicated toward work and try to reply as fast they can. I have hunted more bugs such as CSRF that worth $1000 and other logical issues.
This vulnerability is pretty simple with critical severity and allowed me to grab information of user from guestbook, forums and news. Suppose in case of grabbing users information you just need to paste it where the most of users visit frequently such as latest news section, latest forum posts or if you want to target any particular user then all you have to do is to paste the link in victims guestbook so whenever the user visit his/her guestbook will be a victim.
First they rewarded me $500 for this bug + 500 ESEA points + Profile badge.
but later they increased the payout to $750 -
After submitting this issue they fixed as soon as possible. And I'm glad to work with them. They are really dedicated toward work and try to reply as fast they can. I have hunted more bugs such as CSRF that worth $1000 and other logical issues.










0 comments:
Post a Comment