PlayTime
Its playtime to get more information a cyber play time!
Playstimes
will give a time to quickly learn the fundamental of information
security. As it stand on internet as security thread to find those
thread playtime will help you to secure your product or privacy from unauthentic access. Just see one of the most interesting topic.
Get your world be secure from cyber attack as quickly as possible.
 |
| PlayTime Cyber Information |
These are the top most topic of cyber attack
- SQL Injection - Data Base Injection is one of most finding vulnerability on many insecure interface. It is work on data flaw and can be find in any product which need to interact with database so called DBMS (Data Base Management System).
- Authentication and Session Management - Authentication is mostly used in every field. Login method may not be the most secure way to get access on private content, to secure login method we always take most method as an excuse to secure the login like session authentication.
- Cross Site Scripting And XSS - XSS may not be harmful if admin will do it on there product. But if attacker can find that mistake, even the admin or authorized people can compromise there privacy.
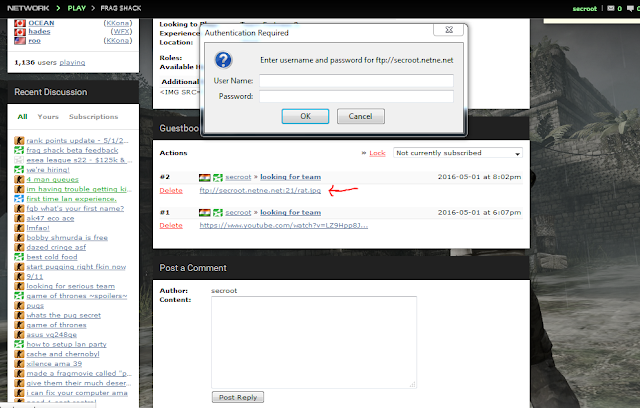
- Direct Object Reference - Direct Object Reference is use as easy for people get the ice cream in there hand. Today's mostly non aware client will take the offer and used the product which is directly accessible.
- Cross Site Request Forgery (CSRF) - CSRF authorized the login and make the session a valid session. There is many example which give the attacker to get access by session.
- Redirection - Redirection is the most harmful attack. Redirection itself cyber attack but when attacker make you read unauthorized data or harmful data will give you a Virus, Trojan and Backdoor.
- Data Exposure - Data content which is not even developer intend to disclose can be accessible and attacker can gain the advantage of that configure data.